Vulnerability analysis is the next phase of Ethical hacking to identify the security holes or vulnerabilities in your system or network. A vulnerability assessment is a process of defining, identifying, classifying and prioritizing vulnerabilities in systems, network infrastructures, and applications. This process provides organizations with the knowledge to understand threats to their environment and react accordingly which provides a way to detect and resolve security problems by ranking the vulnerabilities before someone or something can exploit them. It is important for the security of the organization.
There are type of vulnerability assessments below:
- Active assessments – Which is the process to send request to the live network directly.
- Passive assessments – Which is the process discover vulnerabilities, open ports, and etc without sending request the target hosts.
- External assessments – Here hackers use techniques to find vulnerabilities of system from outside.
- Internal assessments – Here hackers use techniques to find vulnerabilities of system from internally.
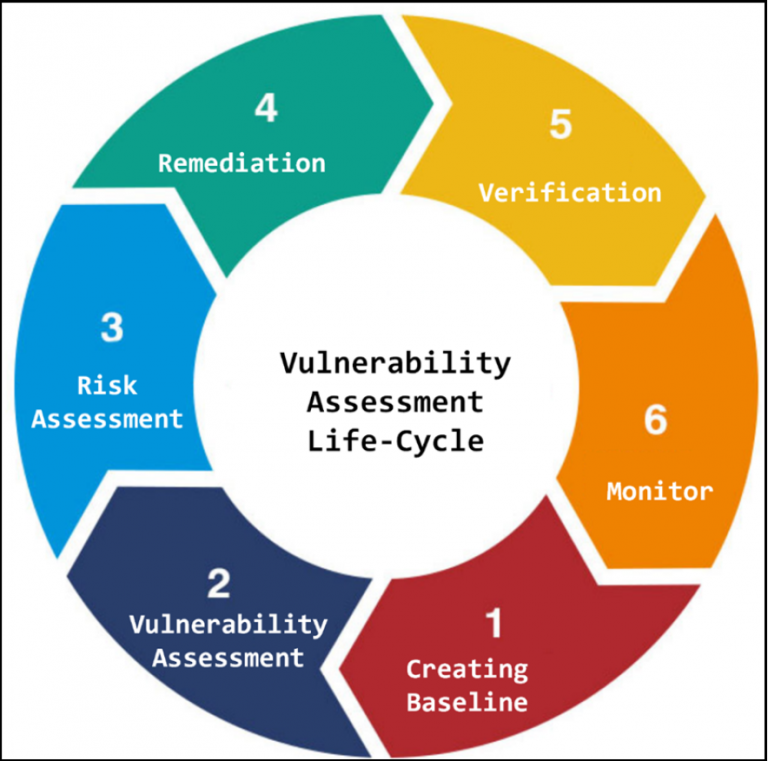
The Vulnerability assessments Life Cycle allow organizations to identify system security weaknesses, prioritize assets, and remediate that and verify that they have been eliminated. There are following phases of the Vulnerability assessments Life Cycle:
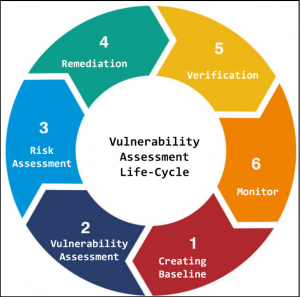
- Creating Baseline – Here performing assessment to find out details including hosts, network, application and other open services.
- Vulnerability Assessment – Here collecting all found vulnerabilities of the system and priorities that .
- Risk Assessment – Here defining the impact of vulnerabilities to an organization
- Remediation – Here prioritize and fix vulnerabilities in order according to business risk
- Verification – Here verifying that all vulnerabilities have been eliminated on organizations.
- Monitor – The end always must monitoring the network and system to avoid unsuspected attacks.
The Common Vulnerability Scoring System (CVSS) provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity. The numerical score can then be translated into a qualitative representation (such as low, medium, high, and critical) to help organizations properly assess and prioritize their vulnerability management processes.
Common Vulnerabilities and Exposure (CVE) is platform which storing information about publicly known cyber security vulnerabilities. CVE Entries are used in numerous cybersecurity products and services from around the world, including the U.S. National Vulnerability Database (NVD). NVD – A vulnerability database built upon and fully synchronized with the CVE List so that any updates to CVE appear immediately in NVD. NVD also provides advanced searching features such as by OS; by vendor name, product name, and/or version number; and by vulnerability type, severity, related exploit range, and impact.
There are many tools for detect vulnerabilities of systems, network and applications. Here listed some tools for vulnerability analysis:
- Nexpose on-premises option for vulnerability management software, monitors exposures in real-time and adapts to new threats with fresh data, ensuring you can always act at the moment of impact.
- Tripwire IP360 allows you to automatically identify assets on your network and their associated vulnerabilities. It then provides granular risk scores based on the severity of the security risk, the ease of exploitation, and the age of the vulnerability.
- Nessus is a commercial vulnerability scanner but they offer free version too.
- Retina Network Security Scanner is a standalone solution designed to discover, profile and assess all assets deployed on an organization’s network. With Retina Network Security Scanner, customers can efficiently identify, prioritize and remediate vulnerabilities such as missing patches and configuration weaknesses.
- OpenVAS is a software framework of several services and tools offering vulnerability scanning and vulnerability management.
- GFI LanGuard is a network security scanner and network monitor with vulnerability management, patch management and application security.
- Qualys Freescan scan your network, servers, desktops and web applications, and detect security vulnerabilities and the patches needed to fix them.
- Aircrack is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security such as Monitoring, Attacking, Testing and Cracking.
- Nikto Web Vulnerability Scanner is a software command-line vulnerability scanner that scans web servers for dangerous files/CGIs, outdated server software and other problems.
- Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education.
- Microsoft Baseline Security Analyzer (MBSA) provides a streamlined method to identify missing security updates and common security misconfigurations(support for Windows 7 and Windows Server 2008 R2. )