After scanning comes enumeration which is direct access to the target system and gets valuable information like as:
- Username information
- Group Information
- Host information
- Network Sharing
- Service information like DNS, NTP, SNMP, SMTP, LDAP, Netbios and etc.
- Network routing information
There are many ways to get that information from the target, the best ones of that are below:
- Get user names using SNMP – SNMP enumeration used to get information like user, group, system device and etc.
- Brute force attack to Active Directory – Attackers always wants to get access to AD. Brute force attacks one of the ways to send queries to LDAP service and get information like username, password and etc.
- Get username using email IDs – email IDs contain information username and domain.
- Get information using default passwords – If the administrator did not change the default password attacker can easily get more information about the system/network.
- Get information using DNS zone transfers – This is to get information like IP address, hostname and etc.
Service Ports for using for enumerating are below:
- DNS – TCP 53 (DNS Zone transfer) and UDP 53 (DNS queries)
- NTP – UDP 123
- SNMP – UDP 161
- SMTP – TCP 25
- LDAP – TCP/UDP 389
- Netbios – TCP 139
NetBIOS Enumeration – NetBIOS names are used to identify network devices, shares, computers, printers over TCP/IP (Windows). It uses a unique 16 ASCII string to identify network devices, 15 characters are used for the device name and the 16th character is identifying the running service.
There are many tools for Netbios enumeration. One of them is nbtstat. Nbtstat is a TCP/IP utility that displays current TCP/IP connections and statistics using NetBIOS over TCP/IP. It is included in several versions of Microsoft Windows and Placed on “C:\Windows\System32\nbtstat.exe”. You can also run that from cmd.exe and see all parameters:
C:\Users\user>nbtstat
Displays protocol statistics and current TCP/IP connections using NBT
(NetBIOS over TCP/IP).
NBTSTAT [ [-a RemoteName] [-A IP address] [-c] [-n]
[-r] [-R] [-RR] [-s] [-S] [interval] ]
-a (adapter status) Lists the remote machine's name table given its name
-A (Adapter status) Lists the remote machine's name table given its
IP address.
-c (cache) Lists NBT's cache of remote [machine] names and their IP addresses
-n (names) Lists local NetBIOS names.
-r (resolved) Lists names resolved by broadcast and via WINS
-R (Reload) Purges and reloads the remote cache name table
-S (Sessions) Lists sessions table with the destination IP addresses
-s (sessions) Lists sessions table converting destination IP
addresses to computer NETBIOS names.
-RR (ReleaseRefresh) Sends Name Release packets to WINS and then, starts Refresh
RemoteName Remote host machine name.
IP address Dotted decimal representation of the IP address.
interval Redisplays selected statistics, pausing interval seconds
between each display. Press Ctrl+C to stop redisplaying
statistics.
For example, nbtstat -a 192.168.100.106 will return following result:
Ethernet: Node IpAddress: [0.0.0.0] Scope Id: [] Host not found. Wi-Fi: Node IpAddress: [192.168.100.106] Scope Id: [] NetBIOS Remote Machine Name Table Name Type Status ——————————————— WORKGROUP <00> GROUP Registered AA-COMP <00> UNIQUE Registered AA-COMP <20> UNIQUE Registered WORKGROUP <1E> GROUP Registered WORKGROUP <1D> UNIQUE Registered ☺☻__MSBROWSE__☻<01> GROUP Registered MAC Address = 74-E5-43-34-B1-E0Every value has its means. Most used values are below:
- 00: Workstation Service (workstation name)
- 03: Windows Messenger service
- 06: Remote Access Service
- 20: File Service (also called Host Record)
- 21: Remote Access Service client
- 1B: Domain Master Browser – Primary Domain Controller for a domain
- 1D: Master Browser
- 00: Workstation Service (workgroup/domain name)
- 1C: Domain Controllers for a domain (group record with up to 25 IP addresses)
- 1E: Browser Service Elections
Another tool for NetBIOS enumeration is the SuperScan tool. It can list a variety of important information dealing with Microsoft Windows such as:
- NetBIOS information
- User and Group Accounts
- Network shares
- Trusted Domains
- Services – which are either running or stopped
To look at network shared resources We can use NET VIEW utility. For example:
C:\Users\user>net view \\192.168.100.106 /ALL
Shared resources at \\192.168.100.106
Share name Type Used as Comment
-------------------------------------------------------------------------------
ADMIN$ Disk Remote Admin
C$ Disk Default share
D$ Disk Default share
IPC$ IPC Remote IPC
The command completed successfully.
Another tool to find shared resources on Network is the SoftPerfect Network Scanner tool. It is a multipurpose network administration tool for Windows and macOS. I downloaded the portable version and scan for my test network IP range:

SNMP(Simple Network Management Protocol) Enumeration – this is an application layer UDP protocol for manage routers, hubs, switches and other network devices on an IP network. SNMP is a common protocol using on Windows, Linux servers, network devices. SNMP is used to enumerate users, groups, passwords, system, devices on a target.
It has 3 components:
- Managed devices – managed devices can be any type of device, like routers, access servers, switches, IP telephones, IP video cameras, computer hosts, printers and etc.
- Agent – An agent is a network-management software on a managed device.
- Network Management System (NMS) executes applications that monitor and control managed devices.
MIB(Management Information Base) are collections of definitions that define the properties of the managed object within the device to be managed. There are 2 types of MIBs: scalar( define a single object instance in MIB tables) and tabular(define multiple related object instances grouped in MIB tables). Object Identifiers(OID) uniquely identify managed objects in a MIB hierarchy. It includes MIB values and settings.
SNMP has 3 version:
- SNMP v1 – this is the 1st version of SNMP. Here the network device and the manager share a secret password and sent in every message in cleartext. A shared password is known as a community string. This is not the best approach in terms of security. This is not supported for encryption and hashing.
- SNMP v2 is an improved form of the first version. The implements a new message known as “GetBulk”. This allows the NMS to efficiently iterate through all the configuration items on the target network device. SNMP v2 allows password hashing with MD5, but this has to be configured.
- SNMP v3 – The latest version of SNMP support for encryption and hashing. SNMPv3 you can specify the level of security you want to. There are 3 options: NoAuthNoPriv( No authentication, No privacy ), AuthNoPriv(Authentication, No privacy) and AuthPriv(Authentication and Privacy).
There are many tools to find SNMP enabled on the network. Let’s to look at this tools.
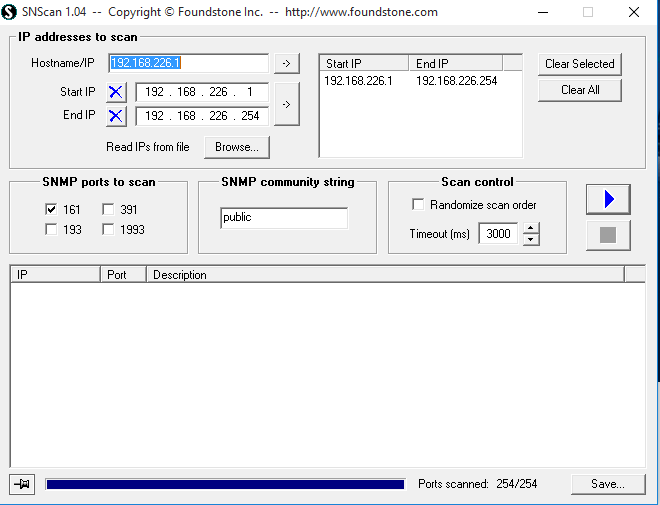
SNScan is a Windows network tool whose purpose is to help you scan and detect SNMP-enabled devices on a network. It is able to indicate devices that are potentially vulnerable to SNMP-related security threats.
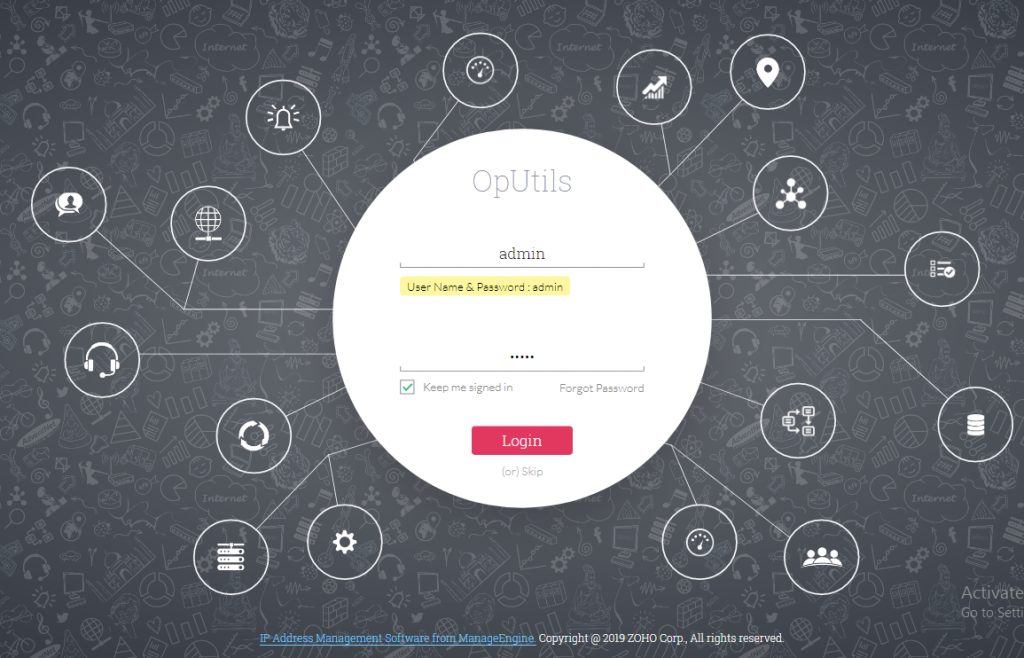
OpUtils is an IP address and Switch port management software helping engineers efficiently monitor, diagnose and troubleshoot IT resources. OpUtils complements existing management tools by providing troubleshooting and real-time monitoring capabilities. One of those tools is SNMP Tools. OpUtils SNMP tools can be used to monitor devices. The MIB database has a huge number of both private and standard vendor MIBs. Using tools such as the walker tool and MIB browser tool, one can monitor any device. Here have tools described as follow:
- MIB Browser – Tool is used to load, browse, search and walk through MIBs, and perform certain basic functions.
- SNMP Graph – Utility to periodically query the given SNMP device for the specified OID value and plot the results in a graph.
- MIB Node Viewer – Utility to provide the details of a particular MIB node and / or the complete details of the selected MIB.
- MIB Module Viewer – Utility to provide a snapshot of a given MIB.
- Community Checker – Utility to detect the read and write community strings of the devices in the network.
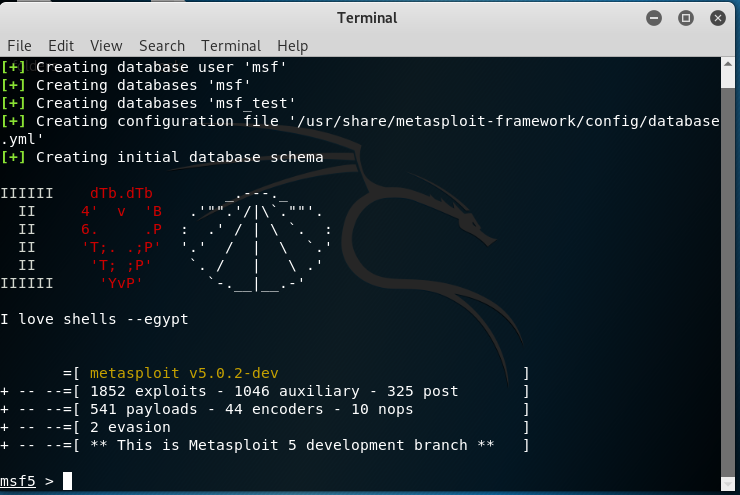
Another tool is the Kali Linux Metasploit tool under Exploitation tools.
After opening tools we will run SNMP enumeration module. Before doing that let’s search relating to SNMP and then find SNMP enumeration module:
msf5> search snmp
msf5> use auxiliary/scanner/snmp/snmp_enum
msf5 auxiliary(scanner/snmp/snmp_enum) > show options
msf5 auxiliary(scanner/snmp/snmp_enum) > set RHOSTS 192.168.100.1 # this is my router
msf5 auxiliary(scanner/snmp/snmp_enum) > run
After these commands, You can see valuable information about your device such as routing information, listening ports, router information, uptime and etc.
Snmpwalk tools in the Kali Linux part and you can get valuable information with helping these tools. You can run snmpwalk on Kali Linux command line and get all option:
root@thehackertips:~# snmpwalk
Created directory: /var/lib/snmp/mib_indexes
No hostname specified.
USAGE: snmpwalk [OPTIONS] AGENT [OID]
Version: 5.7.3
Web: http://www.net-snmp.org/
Email: net-snmp-coders@lists.sourceforge.net
OPTIONS:
-h, --help display this help message
-H display configuration file directives understood
-v 1|2c|3 specifies SNMP version to use
-V, --version display package version number
SNMP Version 1 or 2c specific
-c COMMUNITY set the community string
SNMP Version 3 specific
-a PROTOCOL set authentication protocol (MD5|SHA)
-A PASSPHRASE set authentication protocol pass phrase
-e ENGINE-ID set security engine ID (e.g. 800000020109840301)
-E ENGINE-ID set context engine ID (e.g. 800000020109840301)
-l LEVEL set security level (noAuthNoPriv|authNoPriv|authPriv)
-n CONTEXT set context name (e.g. bridge1)
-u USER-NAME set security name (e.g. bert)
-x PROTOCOL set privacy protocol (DES|AES)
-X PASSPHRASE set privacy protocol pass phrase
-Z BOOTS,TIME set destination engine boots/time
General communication options
-r RETRIES set the number of retries
-t TIMEOUT set the request timeout (in seconds)
Debugging
-d dump input/output packets in hexadecimal
-D[TOKEN[,...]] turn on debugging output for the specified TOKENs
(ALL gives extremely verbose debugging output)
General options
-m MIB[:...] load given list of MIBs (ALL loads everything)
-M DIR[:...] look in given list of directories for MIBs
(default: /root/.snmp/mibs:/usr/share/snmp/mibs:/usr/share/snmp/mibs/iana:/u sr/share/snmp/mibs/ietf:/usr/share/mibs/site:/usr/share/snmp/mibs:/usr/share/mib s/iana:/usr/share/mibs/ietf:/usr/share/mibs/netsnmp)
-P MIBOPTS Toggle various defaults controlling MIB parsing:
u: allow the use of underlines in MIB symbols
c: disallow the use of "--" to terminate comments
d: save the DESCRIPTIONs of the MIB objects
e: disable errors when MIB symbols conflict
w: enable warnings when MIB symbols conflict
W: enable detailed warnings when MIB symbols conflict
R: replace MIB symbols from latest module
-O OUTOPTS Toggle various defaults controlling output display:
0: print leading 0 for single-digit hex characters
a: print all strings in ascii format
b: do not break OID indexes down
e: print enums numerically
E: escape quotes in string indices
f: print full OIDs on output
n: print OIDs numerically
q: quick print for easier parsing
Q: quick print with equal-signs
s: print only last symbolic element of OID
S: print MIB module-id plus last element
t: print timeticks unparsed as numeric integers
T: print human-readable text along with hex strings
u: print OIDs using UCD-style prefix suppression
U: don't print units
v: print values only (not OID = value)
x: print all strings in hex format
X: extended index format
-I INOPTS Toggle various defaults controlling input parsing:
b: do best/regex matching to find a MIB node
h: don't apply DISPLAY-HINTs
r: do not check values for range/type legality
R: do random access to OID labels
u: top-level OIDs must have '.' prefix (UCD-style)
s SUFFIX: Append all textual OIDs with SUFFIX before parsing
S PREFIX: Prepend all textual OIDs with PREFIX before parsing
-L LOGOPTS Toggle various defaults controlling logging:
e: log to standard error
o: log to standard output
n: don't log at all
f file: log to the specified file
s facility: log to syslog (via the specified facility )
(variants)
[EON] pri: log to standard error, output or /dev/nul l for level 'pri' and above
[EON] p1-p2: log to standard error, output or /dev/nul l for levels 'p1' to 'p2'
[FS] pri token: log to file/syslog for level 'pri' and above
[FS] p1-p2 token: log to file/syslog for levels 'p1' to 'p2'
-C APPOPTS Set various application specific behaviours:
p: print the number of variables found
i: include given OID in the search range
I: don't include the given OID, even if no results ar e returned
c: do not check returned OIDs are increasing
t: Display wall-clock time to complete the walk
T: Display wall-clock time to complete each request
E {OID}: End the walk at the specified OID
For example, I run this command to my router: snmpwalk -c public 192.168.100.1 -v1
PRTG software belongs to https://www.paessler.com. With this software, you can do SNMP Monitoring. PRTG comes with several pre-configured SNMP sensors. Among these is a series of sensors developed especially for device manufacturers such as Cisco, HP, Dell, and Synology. The SNMP Custom sensor also lets you monitor a number of other devices from a variety of different manufacturers via SNMP.
LDAP(Lightweight Directory Access Protocol) Enumeration – This is a protocol used to access directory listings within Directory Services. These directory services maybe Active Directory, Open Directory, Open LDAP and etc. LDAP is an open standard internet protocol and using TCP port 389. LDAP is an important part of the system and it stores all user information included the password. Attacker queries LDAP service to gather information such as valid user names, addresses, departmental details and so on.
To enumerate LDAP using many tools and some of them We will look at below.
LDAP Account Manager (LAM) is a web frontend for managing entries like users, groups, DHCP settings stored in an LDAP directory. You can download and use it from https://www.ldap-account-manager.org.
Active Directory Explorer (AD Explorer) is an advanced Active Directory viewer and editor. You can use AD Explorer to easily navigate an AD database, define favorite locations, view object properties and attributes without having to open dialog boxes, edit permissions, view an object’s schema, and execute sophisticated searches that you can save and re-execute. You can download and use it from https://docs.microsoft.com/en-us/sysinternals/downloads/adexplorer.
JXplorer is a cross-platform LDAP browser and editor. It can be used to search, read and edit any standard LDAP directory, or any directory service with an LDAP or DSML interface. You can download and use it from http://jxplorer.org/.
LDAP Admin is a free Windows LDAP client and administration tool for LDAP directory management. This application lets you browse, search, modify, create and delete objects on LDAP server. You can download and use it from http://www.ldapadmin.org.
The LDAP Browser/Editor provides a user-friendly Windows Explorer-like interface to LDAP directories with tightly integrated browsing and editing capabilities. You can download and use it from https://www.novell.com/coolsolutions/tools/13765.html.
NTP(network time protocol) Enumeration – this protocol using to synchronize the time of network devices, computers, servers and etc. It uses UDP port 123. By querying the NTP server you can collect information such as lists of hosts connected to the NTP server, IP addresses, system names, and OSs running on the client system in a network. NTP is intended to synchronize all clients with Coordinated Universal Time (UTC).
ntpdc is used to query the ntpd daemon about its current state and to request changes in that state.
root@thehackertips:~# ntpdc --help
ntpdc - vendor-specific NTPD control program - Ver. 4.2.8p12
Usage: ntpdc [ - [] | --[{=| }] ]... [ host ...]
Flg Arg Option-Name Description
-4 no ipv4 Force IPv4 DNS name resolution
- prohibits the option 'ipv6'
-6 no ipv6 Force IPv6 DNS name resolution
- prohibits the option 'ipv4'
-c Str command run a command and exit
- may appear multiple times
-d no debug-level Increase debug verbosity level
- may appear multiple times
-D Num set-debug-level Set the debug verbosity level
- may appear multiple times
-i no interactive Force ntpq to operate in interactive mode
- prohibits these options:
command
listpeers
peers
showpeers
-l no listpeers Print a list of the peers
- prohibits the option 'command'
-n no numeric numeric host addresses
-p no peers Print a list of the peers
- prohibits the option 'command'
-s no showpeers Show a list of the peers
- prohibits the option 'command'
opt version output version information and exit
-? no help display extended usage information and exit
-! no more-help extended usage information passed thru pager
-> opt save-opts save the option state to a config file
-< Str load-opts load options from a config file
- disabled as '--no-load-opts'
- may appear multiple times
ntptrace is a Perl script that uses the ntpq utility program to follow the chain of NTP servers from a given host back to the primary time source.
root@thehackertips:~# ntptrace --help
ntptrace - Trace peers of an NTP server - Ver. 4.2.8p12
USAGE: ntptrace [ - [] | --[{=| }] ]... [host]
-n, --numeric Print IP addresses instead of hostnames
-m, --max-hosts=num Maximum number of peers to trace
-r, --host=str Single remote host
-?, --help Display usage information and exit
--more-help Pass the extended usage text through a pager
Options are specified by doubled hyphens and their name or by a single
hyphen and the flag character.
The ntpq utility program is used to query NTP servers.
root@thehackertips:~# ntpq --help
ntpq - standard NTP query program - Ver. 4.2.8p12
Usage: ntpq [ - [] | --[{=| }] ]... [ host ...]
Flg Arg Option-Name Description
-4 no ipv4 Force IPv4 name resolution
- prohibits the option 'ipv6'
-6 no ipv6 Force IPv6 name resolution
- prohibits the option 'ipv4'
-c Str command run a command and exit
- may appear multiple times
-d no debug-level Increase debug verbosity level
- may appear multiple times
-D Num set-debug-level Set the debug verbosity level
- may appear multiple times
-i no interactive Force ntpq to operate in interactive mode
- prohibits these options:
command
peers
-n no numeric numeric host addresses
no old-rv Always output status line with readvar
-p no peers Print a list of the peers
- prohibits the option 'interactive'
-r KWd refid Set default display type for S2+ refids
-w no wide Display the full 'remote' value
opt version output version information and exit
-? no help display extended usage information and exit
-! no more-help extended usage information passed thru pager
-> opt save-opts save the option state to a config file
-< Str load-opts load options from a config file
- disabled as '--no-load-opts'
- may appear multiple times
SMTP Enumeration – The Simple Mail Transport Protocol is used to send email messages and using port 25. SMTP enumeration allows us to determine valid users on the SMTP server and done with the help SMTP commands:
- VRFY – is used for validating users.
- EXPN – command tells the actual delivery address of aliases and mailing lists.
- RCPT – defines the recipients of the message.
- HELO – sent by a client to introduce itself.
- EHLO – another way of client introducing itself to server
- HELP – used to see all commands.
- DATA – sent by a client to initiate data transfer.
- QUIT – to end the session.
Every command will receive a reply from the mail server, some of them as follows:
- 220 – Server is ready
- 221 – The server is closing its transmission channel
- 250 – Requested mail action okay completed
- 251 – User not local will forward
- 252 – Cannot verify the user, but it will try to deliver the message anyway
- 354 – Start mail input
Let’s take a look at some SMTP tools:
root@thehackertips:~# nslookup mail.thehackertips.com
Server: 192.168.226.2
Address: 192.168.226.2#53
Non-authoritative answer:
Name: mail.thehackertips.com
Address: 66.96.144.191
root@thehackertips:~# telnet mail.thehackertips.com 25
Trying 66.96.144.191…
Connected to mail.thehackertips.com.
# you can use SMTP commands to send request to server.
root@thehackertips:~# smtp-user-enum
smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
Usage: smtp-user-enum [options] ( -u username | -U file-of-usernames ) ( -t host | -T file-of-targets )
options are:
-m n Maximum number of processes (default: 5)
-M mode Method to use for username guessing EXPN, VRFY or RCPT (default: VRFY)
-u user Check if user exists on remote system
-f addr MAIL FROM email address. Used only in "RCPT TO" mode (default: user@example.com)
-D dom Domain to append to supplied user list to make email addresses (Default: none)
Use this option when you want to guess valid email addresses instead of just usernames
e.g. "-D example.com" would guess foo@example.com, bar@example.com, etc. Instead of
simply the usernames foo and bar.
-U file File of usernames to check via smtp service
-t host Server host running smtp service
-T file File of hostnames running the smtp service
-p port TCP port on which smtp service runs (default: 25)
-d Debugging output
-t n Wait a maximum of n seconds for reply (default: 5)
-v Verbose
-h This help message
Also see smtp-user-enum-user-docs.pdf from the smtp-user-enum tar ball.
Examples:
$ smtp-user-enum -M VRFY -U users.txt -t 10.0.0.1
$ smtp-user-enum -M EXPN -u admin1 -t 10.0.0.1
$ smtp-user-enum -M RCPT -U users.txt -T mail-server-ips.txt
$ smtp-user-enum -M EXPN -D example.com -U users.txt -t 10.0.0.1
root@thehackertips:~# smtp-user-enum -M RCPT -u user@thehackertips.com -t mail.thehackertips.com
Starting smtp-user-enum v1.2 ( http://pentestmonkey.net/tools/smtp-user-enum )
| Scan Information |
Mode ………………… RCPT
Worker Processes ……… 5
Target count …………. 1
Username count ……….. 1
Target TCP port ………. 25
Query timeout ………… 5 secs
Target domain …………
## Scan started at Sun Nov 17 11:30:50 2019
## Scan completed at Sun Nov 17 11:30:51 2019
0 results.
1 queries in 1 seconds (1.0 queries / sec)
DNS Enumeration – DNS enumeration is one way of finding DNS servers and their records for an organization. There are internal and external DNS servers that can hold information like usernames, hosts and IP addresses of potential target systems. There are a lot of tools that can be used to gain information noted above. DNS uses TCP 53 (DNS Zone transfer) and UDP 53 (DNS queries) ports. DNS enumeration can also happen through DNS zone transfer. The attacker can find and seize the DNS server with TCP port 53 and copy the database to another server.
Let’s try some command to get DNS information:
################# Windows command line #############
C:\Users\user>nslookup
DNS request timed out.
timeout was 2 seconds.
Default Server: UnKnown
Address: 192.168.100.1
> set type=any
> thehackertips.com
Server: UnKnown
Address: 192.168.100.1
Non-authoritative answer:
thehackertips.com text =
"v=spf1 ip4:66.96.128.0/18 ?all"
thehackertips.com MX preference = 30, mail exchanger = mx.thehackertips.com
thehackertips.com
primary name server = ns1.yourwebhosting.com
responsible mail addr = dnsadmin.yourwebhosting.com
serial = 2019090837
refresh = 10800 (3 hours)
retry = 3600 (1 hour)
expire = 604800 (7 days)
default TTL = 3600 (1 hour)
thehackertips.com internet address = 66.96.144.191
thehackertips.com nameserver = ns2.yourwebhosting.com
thehackertips.com nameserver = ns1.yourwebhosting.com
mx.thehackertips.com internet address = 66.96.140.139
mx.thehackertips.com internet address = 66.96.140.138
ns1.yourwebhosting.com internet address = 66.96.142.112
ns2.yourwebhosting.com internet address = 65.254.254.147
################ Kali Linux ##########################
root@thehackertips:~# nslookup thehackertips.com
Server: 192.168.226.2
Address: 192.168.226.2#53
Non-authoritative answer:
Name: thehackertips.com
Address: 66.96.144.191
root@thehackertips:~# nslookup
set type=any
thehackertips.com
Server: 192.168.226.2
Address: 192.168.226.2#53
Non-authoritative answer:
thehackertips.com text = "v=spf1 ip4:66.96.128.0/18 ?all"
thehackertips.com mail exchanger = 30 mx.thehackertips.com.
thehackertips.com
origin = ns1.yourwebhosting.com
mail addr = dnsadmin.yourwebhosting.com
serial = 2019090837
refresh = 10800
retry = 3600
expire = 604800
minimum = 3600
Name: thehackertips.com
Address: 66.96.144.191
thehackertips.com nameserver = ns2.yourwebhosting.com.
thehackertips.com nameserver = ns1.yourwebhosting.com.
Authoritative answers can be found from:
thehackertips.com nameserver = ns2.yourwebhosting.com.
thehackertips.com nameserver = ns1.yourwebhosting.com.
mx.thehackertips.com internet address = 66.96.140.138
mx.thehackertips.com internet address = 66.96.140.139
ns1.yourwebhosting.com internet address = 66.96.142.112
ns2.yourwebhosting.com internet address = 65.254.254.147
root@thehackertips:~# dig thehackertips.com any
; <<>> DiG 9.11.5-P1-1-Debian <<>> thehackertips.com any
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 39258
;; flags: qr rd ra; QUERY: 1, ANSWER: 6, AUTHORITY: 2, ADDITIONAL: 5
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1280
;; QUESTION SECTION:
;thehackertips.com. IN ANY
;; ANSWER SECTION:
thehackertips.com. 3027 IN TXT "v=spf1 ip4:66.96.128.0/18 ?all"
thehackertips.com. 3027 IN MX 30 mx.thehackertips.com.
thehackertips.com. 3027 IN SOA ns1.yourwebhosting.com. dnsadmin.yourwebhosting.com. 2019090837 10800 3600 604800 3600
thehackertips.com. 2518 IN A 66.96.144.191
thehackertips.com. 3027 IN NS ns1.yourwebhosting.com.
thehackertips.com. 3027 IN NS ns2.yourwebhosting.com.
;; AUTHORITY SECTION:
thehackertips.com. 3027 IN NS ns1.yourwebhosting.com.
thehackertips.com. 3027 IN NS ns2.yourwebhosting.com.
;; ADDITIONAL SECTION:
mx.thehackertips.com. 3027 IN A 66.96.140.138
mx.thehackertips.com. 3027 IN A 66.96.140.139
ns1.yourwebhosting.com. 52799 IN A 66.96.142.112
ns2.yourwebhosting.com. 52799 IN A 65.254.254.147
;; Query time: 109 msec
;; SERVER: 192.168.226.2#53(192.168.226.2)
;; WHEN: Sun Nov 17 11:47:23 EST 2019
;; MSG SIZE rcvd: 312