This is the first step in Ethical Hacking. It is a collection of information about the target. There are active (directly with target) and passive (indirectly with target) methods of reconnaissance. An ethical hacker must know security posture, reduce focus area, identify vulnerabilities and draw network maps in this phase.
An ethical hacker can gather enough information used footprinting techniques listed below:
- Search Engines
- Google Hacking
- Social Networking
- Websites of the company
- Email footprinting
- Whois
- DNS
- Network footprinting
- Social Engineering
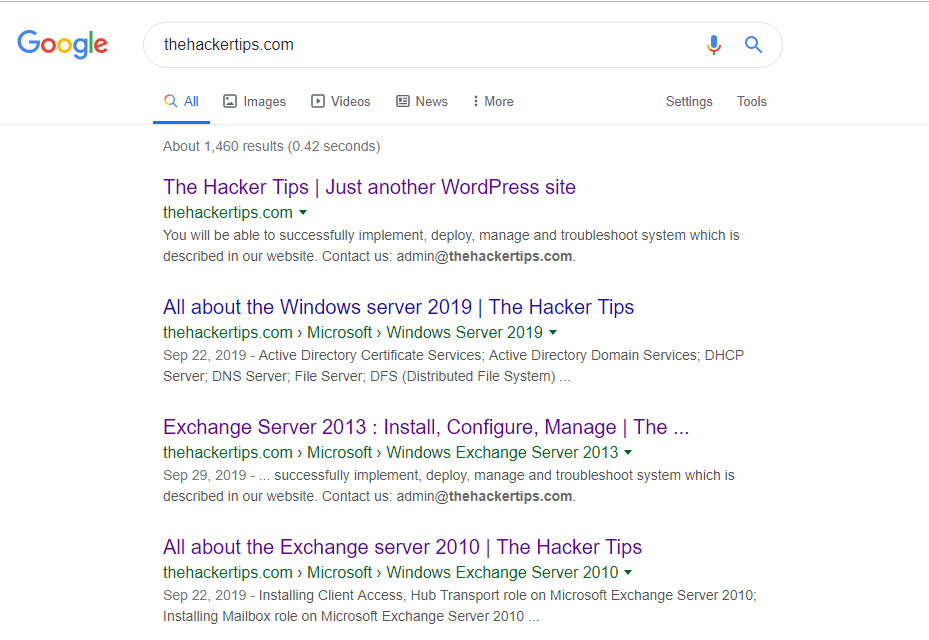
With Footprinting through Search engine techniques, You can open any search engine and search about the target. Here you will find the most basic information about the target. You can also use different services to collect information about the target.
Ethical hackers can also collect the physical location of the target by helping online map services like as: Google map, yahoo map, Bing map and etc.
Also possible get important information through job sites like as linkedin.com, indeed.com. Here possible collect valuable information like contact information, IT jobs requirements(hardware and software) about the target.
Google Hacking techniques help to search for a specific topic. There are search operators which used for that:
- Site – Search for specific domain
- Related: search for web pages
- cache: search web pages which stored in a cache
- link: get the websites which having specific webpages
- allintext: search website containing specific keywords
- intext: search for documents containing specific keywords
- allintitle: search website containing specific keywords in the title
- intitle: search for documents containing specific keywords in the title
- allinurl: search website containing specific keywords in URL
- inurl: search for documents containing specific keywords in URL
You can also go to the following URL for Advanced search: https://www.google.com/advanced_search
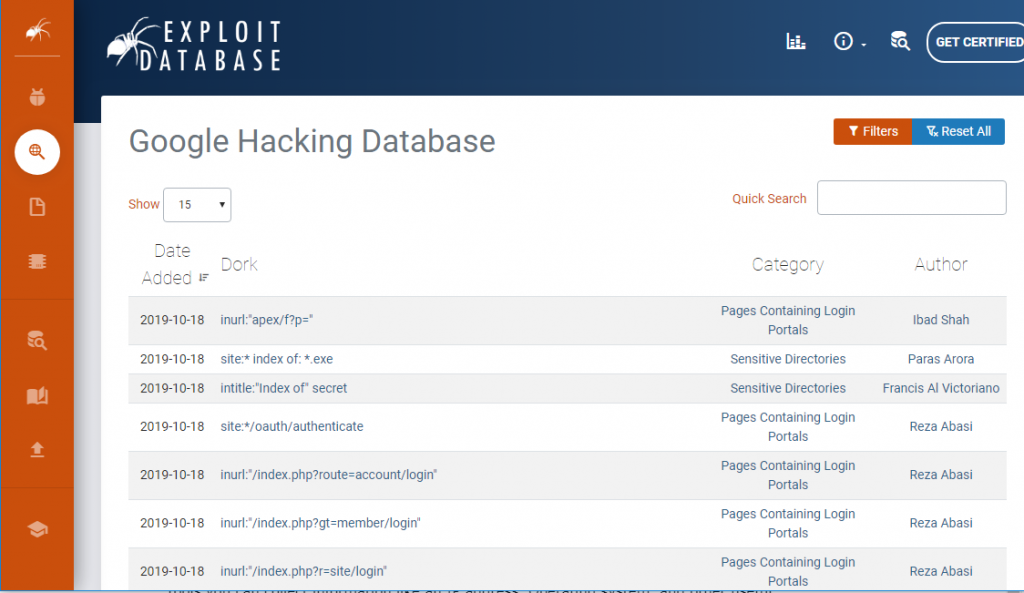
Google hacking is used to speed up search and all these queries categorized the database known as Google hacking database(GHDB) by Johnny Long. With this link https://www.exploit-db.com/google-hacking-database you can reach the GHDB.
Social Networking websites easily help to get information about the target. You can use facebook, twitter, linkedin, Instagram, and other popular social networking and get information like a contact number, email address, location, date of birth, workplace and much more.
The company Website gives a lot of information about the target. Using online or offline tools you can collect information like an IP address, Operating system, and other useful information. Ethical Hacker can use techniques below for this purpose:
- Netcraft.com – all information about the domain, operating system and etc.
- shodan.io – find connected network devices like router, server and etc.
- Web data extractor application -Web spiders
- Mirroring website tools: Win HTTrack Website Copier – www.httrack.com, Website Ripper Copier – www.tensons.com
- web.archive.org – online platform old version of websites.
- Website Watcher application – help to check website updates
- Website monitoring tools – onwebchange.com, watchthatpage.com
- Website traffic monitoring tools – Alexa.com, web-stat.com, monitis.com
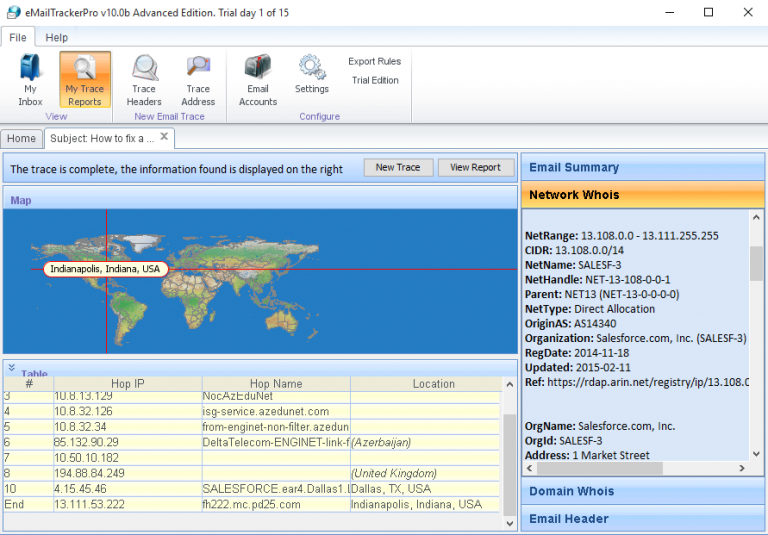
All companies have their email service. Because of that email footprinting play more important roles to get information about the target. For example with simple mail can be sent the malicious links to target and can get information like an IP address, email server and etc. Also, have some email tracking tools which help to get more information.
- Email Tracking Pro – www.emailtrackerpro.com – trace the email header
- politemail.com
- contactmonkey.com
- pointofmail.com

WHOIS footprinting helps an Ethical hacker to get information about an IP address, DNS server, domain status, organization, and other information. Whois Kali Linux command is used to identify that information and Also with www.whois.com and whois.domaintools.com websites can be collected all of that.
Also, you can download SmartWhois application from https://www.tamos.com/download/main/ and collect whois information.

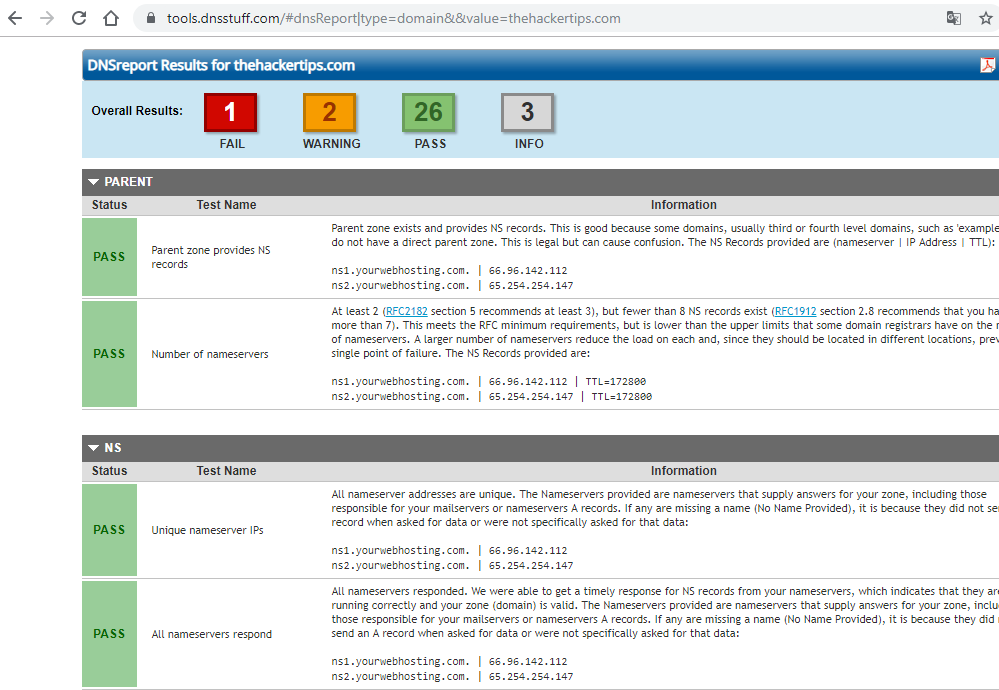
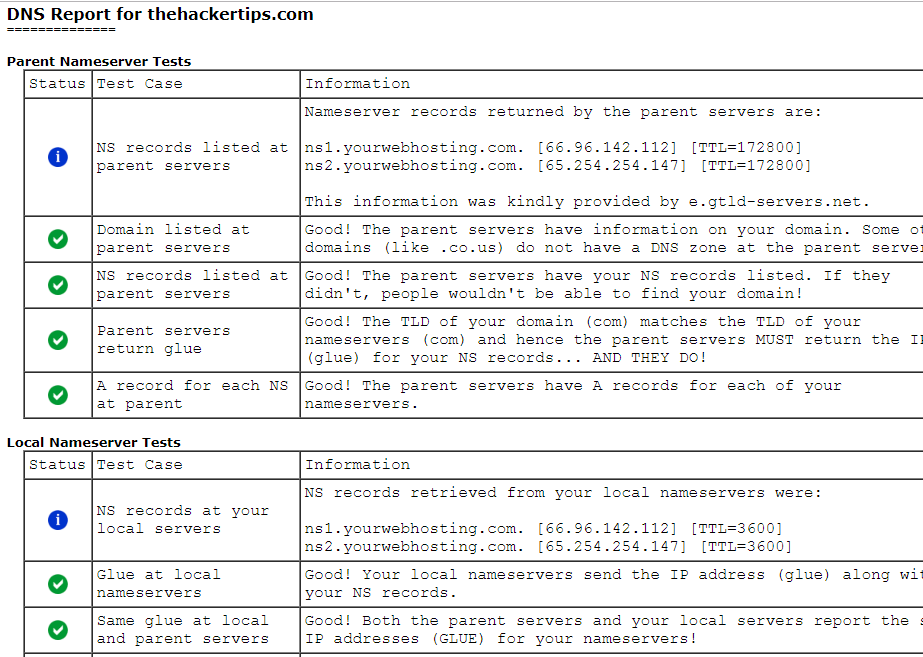
DNS lookup help to get all DNS related record(A, MX, NS, SRV, PTR, TXT and etc.) and identify other targeted networks. You can use the online tools listed below:
- tools.dnsstuff.com
- centralops.net/co/
- dnsqueries.com
- ultratools.com
- viewdns.info
- network-tools.com
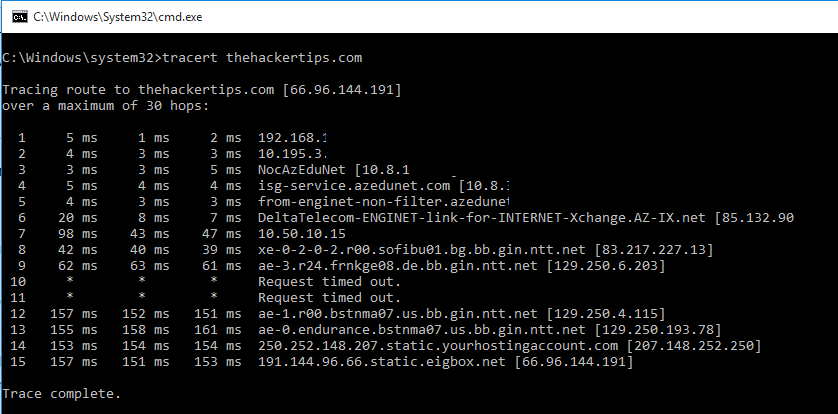
Network footprinting is important to get information about the target network. You can use network tools to get information such as: hostname, IP address, hosts and etc.
- Tracert – get path information from source to target. You can also use some online or software for this case(www.pathanalyzer.com, www.visualroute.com).
- Ping
- nslookup
At the present time, Social Engineering is one of the most used types of footprinting. An attacker can easily collect usernames, passwords, credit card information and other sensitive information. One of the most used techniques is phishing. In this case, the Attacker sends email to target with malicious link or files which looks legitimate. After the recipient click the link and it redirects to a fake webpage for entering sensitive information like username and passwords.
One of the most used footprinting tools is Maltego – www.paterva.com. Maltego is an interactive, visual data mining and link analysis tool used to conduct online investigations.

Metagoofil is the tool designed for extracting metadata of public documents (pdf,doc,xls,ppt,docx,pptx,xlsx) belonging to a target company. This tool included in the metagoofil package in Kali Linux and described below:
root@kali:~# metagoofil
Usage: metagoofil options
-d: domain to search
-t: filetype to download (pdf,doc,xls,ppt,odp,ods,docx,xlsx,pptx)
-l: limit of results to search (default 200)
-h: work with documents in directory (use "yes" for local analysis)
-n: limit of files to download
-o: working directory (location to save downloaded files)
-f: output file
Examples:
metagoofil.py -d apple.com -t doc,pdf -l 200 -n 50 -o applefiles -f results.html
metagoofil.py -h yes -o applefiles -f results.html (local dir analysis)
Scan for documents from a domain (-d thehackertips.com) that are PDF files (-t pdf), searching 50 results (-l 50), download 5 files (-n 5), saving the downloads to a directory (-o thehackerpdf), and saving the output to a file (-f hackerpdf.html):
root@kali:~# metagoofil -d thehackertips.com -t pdf -l 50 -n 5 -o thehackerpdf -f hackerpdf.html
['pdf']
[-] Starting online search...
[-] Searching for pdf files, with a limit of 50
Searching 50 results...
Results: 36 files found
Starting to download 5 of them