Graylog allows to receive SYSTEM, THREAT and TRAFFIC logs directly from a Palo Alto device and the Palo Alto Panorama system. We will use UDP 5241 port for logging.
Login to Paloalto firewall and create a syslog server profile:
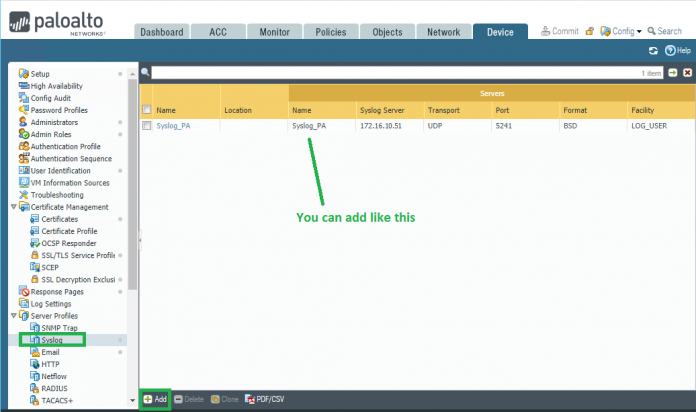
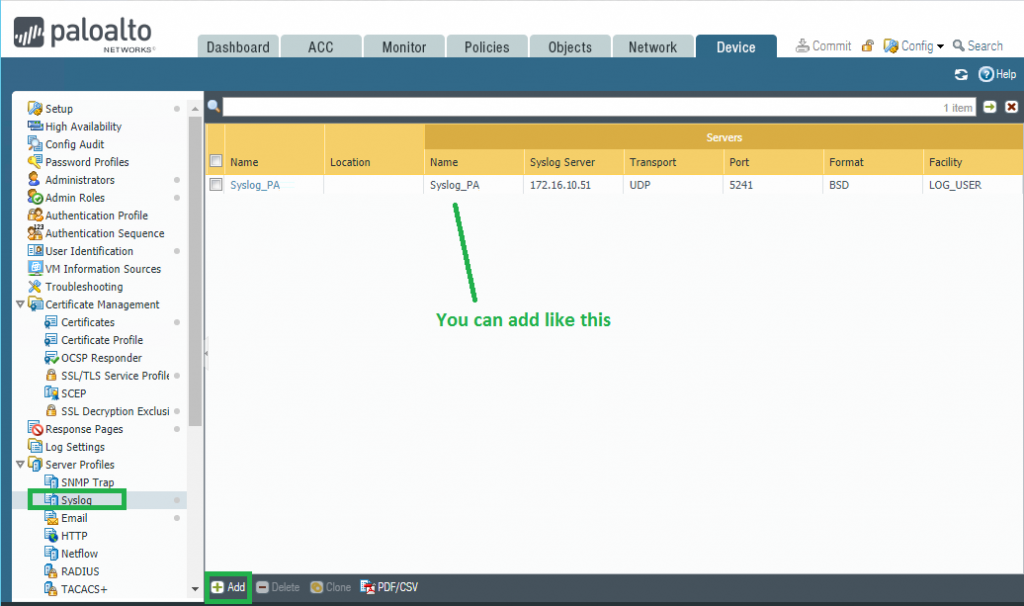
Go to Device > Server Profiles > Syslog and add syslog server profile:
You need to fill following information:
- Name : Enter a name for the syslog profile (up to 31 characters). The name is case-sensitive and must be unique. Use only letters, numbers, spaces, hyphens, and underscores.
- Name : Click Add and enter a name for the syslog server (up to 31 characters). The name is case-sensitive and must be unique. Use only letters, numbers, spaces, hyphens, and underscores.
- Syslog Server: Enter the IP address of the syslog server.
- Transport: Select whether to transport the syslog messages over UDP, TCP, or SSL.
- Port: Enter the port number of the syslog server (the standard port for UDP is 514; the standard port for SSL is 6514; for TCP you must specify a port number).
- Format: Specify the syslog format to use: BSD (the default) or IETF.
- Facility: Select one of the Syslog standard values. Select the value that maps to how your Syslog server uses the facility field to manage messages. For details on the facility field, see RFC 3164 (BSD format) or RFC 5424 (IETF format).
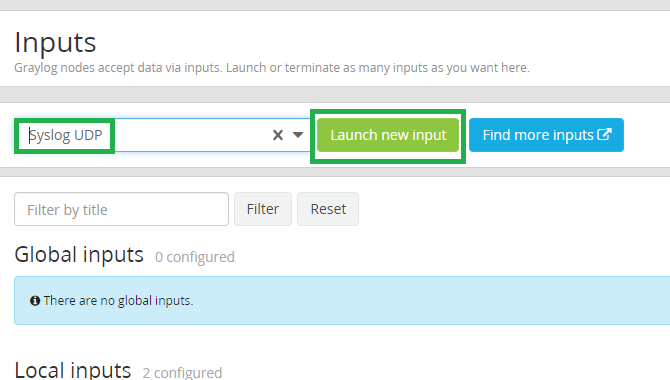
We finish configuration on Paloalto firewall. Now we can move to graylog server to create input to receive logs. Message inputs are the Graylog parts responsible for accepting log messages.There are many inputs that support graylog and We will use SYSLOG UDP.
So login to graylog and go to System -> Inputs, choose syslog udp from the list and click on Launch new input
Then fill all required field as below and click Save:
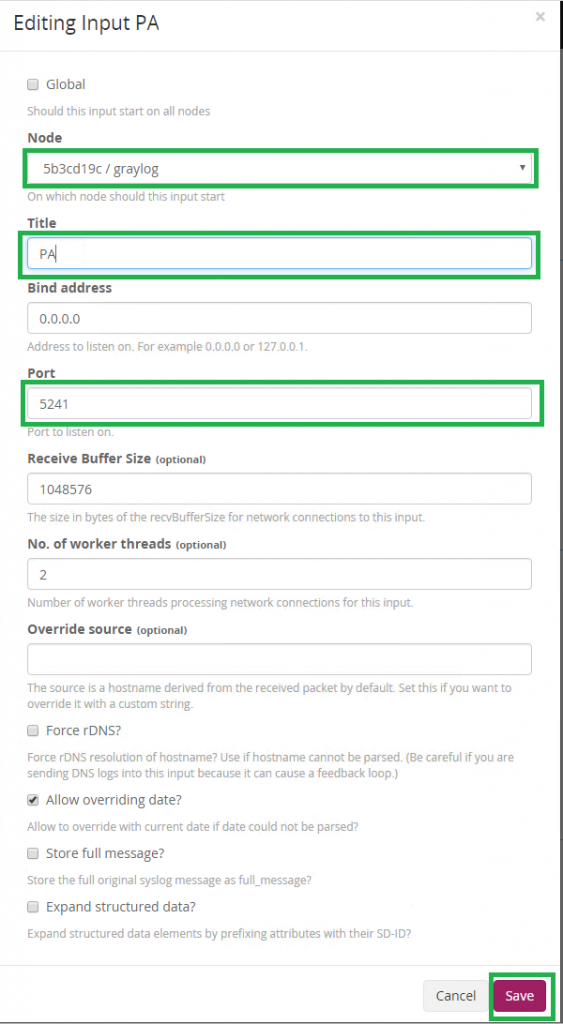
Click “Show received messages” to look at logs:

That’s all. I hope, this article was helpful for you and You can look at other articles about graylog from here Graylog log management